11 Top Web Application Security Best Practices for Your Business
In this web application development universe, unexpected growth has been observed in the last decade. Till the year 2015, the majority of business owners used to keep mobile applications as their priority. However, after 2015, business owners are moving to web application development to target their audiences.
According to Emergen Research, the progressive web application development market indicated a growth of 31.9% CAGR for the time period 2017 to 2027. In this year 2019, this market was valued at $ 1.13 billion.
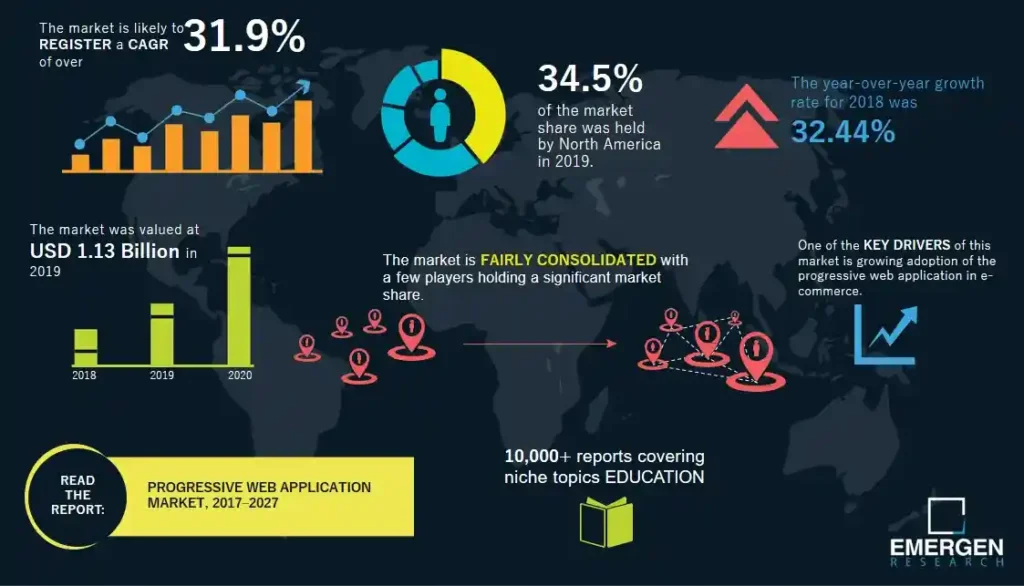
With reference to the above research, it can be clear that the web application market incorporates a huge growth potential. However, with each new technology, security is a prime concern of every business owner. It is also a fact that companies or business owners want to manifest their idea of developing web apps but they are concerned about the security parameters.
So, at Amplework, we decided to ease all your worries related to the security parameters of web apps. In this blog, we’re covering the discussion for the top 11 web application security practices which will help you to keep your web apps highly secure and profound.
Top 11 Web Security Parameters
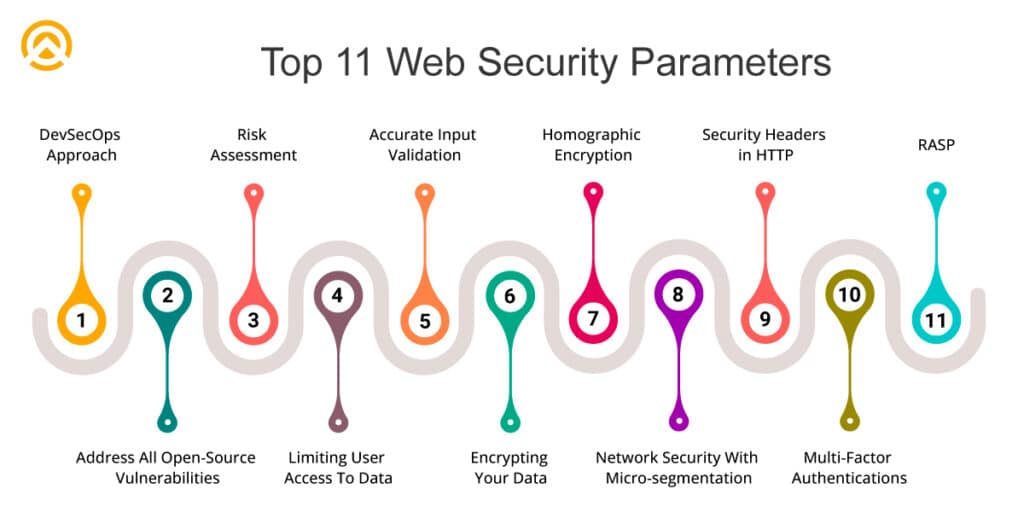
While incorporating web application development services, you should go for these top 11 suggested security parameters. At Amplework, we support our clients during each stage of operations and we make sure to include cutting-edge web security parameters for transforming business processes:
Top 1: Adapt a DevSecOps Approach
DevSecOps emphasizes the automation of security practices, such as continuous security testing, code analysis, and vulnerability scanning. This enables organizations to detect and address security issues in real time, reducing the chances of vulnerabilities going unnoticed. By incorporating security into the development process from the beginning, organizations can build more robust and secure applications, protecting sensitive data and maintaining the trust of their users.
Top 2: Need to Address All Open-Source Vulnerabilities
Open-source vulnerabilities arise from a variety of factors, including outdated dependencies, weak encryption algorithms, or inadequate security configurations. Attackers often exploit these vulnerabilities to gain unauthorized access, compromise data integrity, or launch attacks on other connected systems. Therefore, it is essential for organizations to regularly update and patch open-source components, monitor security advisories, and conduct thorough security assessments of their software stack.
Implementing vulnerability management processes, such as regular vulnerability scans and penetration testing, can help identify and prioritize open-source vulnerabilities. Additionally, organizations should establish clear procedures for promptly addressing and mitigating identified vulnerabilities, including patching or upgrading affected components. By actively managing open-source vulnerabilities, organizations can reduce the risk of security breaches and protect their systems and data from potential threats.
Top 3: Risk Assessment
Conducting comprehensive risk assessments is a critical aspect of effective security practices. Risk assessment involves identifying, evaluating, and prioritizing potential threats and vulnerabilities to an organization’s systems, applications, and data. By conducting regular risk assessments, organizations can make informed decisions regarding security measures and resource allocation to mitigate risks effectively.
A robust risk assessment process typically involves several key steps. Firstly, organizations should identify and document their assets, including hardware, software, data, and personnel. They should then assess and classify the criticality and sensitivity of these assets to determine potential impacts in the event of a security breach. Web application developers will help you to conduct a proper risk assessment for handling issues.
Top 4: Limiting User Access To Data
One crucial aspect of ensuring data security is limiting user access to sensitive information. Not all users within an organization require access to all data, and providing excessive privileges can increase the risk of unauthorized access, data breaches, and insider threats. Therefore, implementing strong access control measures is essential to safeguard sensitive data and maintain confidentiality.
Top 5: Encrypting Your Data
It is always the best option to keep your data in encryption format. Only those users will get the access to data who incorporated an authorized encryption key and completely protected their data.

Top 6: Accurate Input Validation
As input validation is the process of testing various inputs that are being received by the application. The interesting part is that it can be extremely easy just like typing a specific parameter and it can be highly complex like utilizing it as a regular expression to validate input.
A web application development company can make use of two different types of input validation – such as:
- Whitelist Validation.
- Blacklist Validation.
Top 7: Utilizing Run-Time Application With Self-Protection Technologies (RASP)
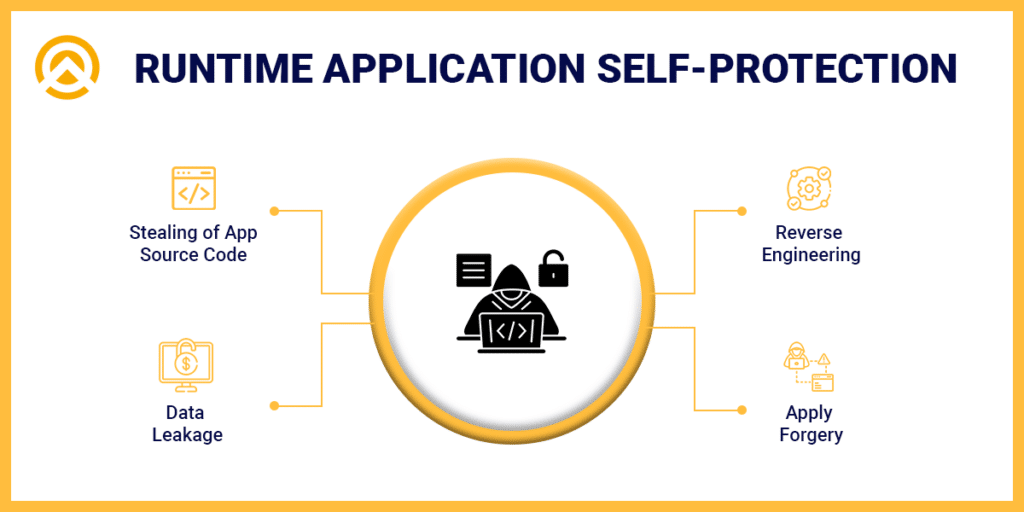
An advanced security solution that is used for ensuring the security of each application. It is designed to provide personalized protection to applications. It even allows real-time monitoring and detection for identifying mobile apps’ runtime behavior.
As the working of RASP ensures the installation of sensors within the code base for monitoring and controlling the execution of the entire application. These sensors also ensure complete visibility of both the application architecture and its execution during runtime.
There are various benefits of RASP security benefits – such as: contextual awareness, visibility into application-layer attacks, lower false positives, zero-day protection, etc. As far as maintenance is concerned then RASP offers easy maintenance for handling operations.
Top 8: Homographic Encryption for Self-Access Control
Many clients asked us to tell them about a way for data modeling without even causing any risk of discovery. At Amplework, we suggest they go for homographic encryption. As homographic encryption is the result of computations that usually remain in encrypted forms. It uses a public key for encryption and a private key for decryption.
If you’re searching for secure and affordable enterprise web development solutions then you should consider Amplework. Our prowess developers ensure to present a secure solution to you by utilizing innovative metrics such as: homographic encryption, data encryption and more.
Top 9: Enhancing Network Security With Micro-segmentation
Web application developers can make use of micro-segmentation to enhance the security of their web applications. If you’re unfamiliar with this concept then we are here to help you. Micro-segmentation is an approach to network security that involves dividing a network into smaller, isolated segments or zones.
Each segment or micro-segment, contains a specific set of resources or assets and has its own security policies and controls. Web application development companies incorporate this technique because it provides granular control over network traffic in several ways.
1. Reduce Attack Surface.
2. Strict Access Controls.
3. Isolation of Critical Assets.
4. Enhanced Visibility & Monitoring.
5. Containment of Threats.
6. Compliance and Regulatory Requirements.
7. Simplification of Security Management.
Top 10: Security Headers in HTTP
To configure a proper security defense in web browsers it is important to make use of security headers. As these security heads are known as directives. Based on these directives, browsers can make it harder for exploiting client-side vulnerabilities.
Here, an argument can arise in your mind that why it is necessary to opt for an HTTP security header? These security headers will be going to protect your website through common attacks such as: XSS, code injection, clickjacking, etc. At Amplework, we offer a wide range of solutions to protect your web against various web attacks.
At Amplework, sometimes our clients raise a common question: what will happen if there will be no HTTP security header in their web apps? Suppose, if there is no HTTP security header then it increases the probability that your users can navigate to an unencrypted version of the web application.
Top 11: Focusing on Multi-Factor Authentications
The use of multi-factor authentication enables the users to pass the authentication test in 3-4 stages. At Amplework, we expert developers always make sure to add multi-factor authentication because it provides a full-proof authentication and only authorized parties can access a specific domain.
If you’re not aware of this security method then let’s read this example – suppose user “x” login to your e-commerce web app. To login into your web app, “X” only needs to enter a specific id/password and he can access his account. Now, suppose that your e-commerce web app incorporates two-factor authentication. In this case, “X” needs to enter his id/password and then “X” also needs to enter a mobile OTP to login. So, we can analyze that “X” will need to enter his id/password as well as a mobile OTP to login.
Here, it is important to understand that two-factor authentication not only works for web apps but it is also used for mobile applications. So, if you’re planning for mobile app development services then you should demand 2-factor authentication to secure users profiles.
The Final Words
In order to secure your custom web application development process you should rely on all the relevant security measures. At Amplework, we consider security as paramount & our prowess developers also incorporate verified security measures to secure all tech solutions. We’re an ISO-certified organization and we’re known in the industry for delivering innovative solutions with all the security measures to leave no room for any authorized access.



 sales@amplework.com
sales@amplework.com
 (+91) 9636-962-228
(+91) 9636-962-228