Be wise & Prioritize: Taking Application Security to the Next Level
There is an ample number of vulnerabilities that continue to get the best software development. Along with the application and the security, teams get increasingly the best vulnerability of the detection tools throughout various development. The maximum level of protection is available and nothing turns out to be unbreakable and un hackable. The latest DevOps tools are used in different processes. Thus priorities should be about taking the best application and security which can be taken to the next level.
Security of the application
The software application is rightly the weakest link that comes out to the security of the enterprises and its stack. The s application security is highly effective and the external attacks matter a lot when it is to software vulnerabilities. Thus, the security of the application is measured in meters. The application level is something that creates the difference.
It is all about taking security to the next level where there will be no disturbance at all. Once users can detect the vulnerabilities, they will need to find a way that can prioritize the activities. It is all about how software development might need to pose a difference. It is all about how the organizations can determine the securities of the vulnerabilities. Immediate attention can develop and secure the activities of the wasting of the vulnerabilities. Is it not a bigger threat?
Vulnerability Prioritization Methods: To each their own?
We asked the customers about how they can prioritize and also find the right risk. Also, the vulnerability of the risk can secure the activities that can determine the risk. The application type where the vulnerability was identified seems to be determined by the severity, combined with the software project. The prioritization methods have their merits that are still far from each other.
The following are the prioritization methods that can earn great features:
#1 Severity
CVSS ratings determine that can be issued attending the critical along with high severity issues. Relying solely on the parameter is problematic for various reasons. The distribution for each level is uneven.60 percent of the vulnerabilities, or roughly. 60 percent of the system, is compromised by the high and seriously developed vulnerabilities. It leaves the team with quite a long list and the security alerts leading to addresses. The attempts of the CVSS are about how it impacts the security indicating the right risk. The risk depends on how the impact times links with likelihood.
#2 Application Type
The teams must prioritize urgent or delicate requests in all other circumstances. These, however, aren’t always the most typical objectives. A further issue with using this approach is that it is challenging to create a technique based on this metric since different firms must deal with various, subjective aspects, including the user audience, the mobile or online application, and more.
#3 Popularity
Some teams consider the popularity of the vulnerability component while deciding the requirement. This is done for immediate attention figuring out the best target for hackers and their community. There is an additional parameter that happens to be one of the key components in the world of structure. It determines the factor when it is about coming down to vulnerability risk level. Popularity is only about the concept of the determining factors.
#4 Disclosure date
Cyber security is a feature that increases the open-source components that force organizations to adjust to security practices. The additional and new frameworks link it with containers and the API aiding the complexity of the application along with its security. In addition to the framework, various options can be developed under pressure. It is to continue the release of the new features. The complication of the security and the application happens to be one of the APIs.
Unfortunately, according to Verizon’s Data Breach Investigations Report (DBIR): “Hackers use what works, and what works doesn’t seem to change all that often. Secondly, attackers automate certain weaponized vulnerabilities and spray and pray them across the internet, sometimes yielding incredible success.”
#5 Ease of Remediation
The popular method is to prioritize the vulnerabilities that are easiest to fix and manage the application quite well. It is time to address the small amount of time guaranteeing the address on the most urgent basis. To get a stronger result one needs to take good care of the common practices for the organizations. It can handle the hefty backlog with alerts to wipe the slate.
It creates the arbitrary point to cut off the run-off need with the reports for Verizon’s Data Breach Investigations Report. Hackers can use the work that works with the same concept and is too often great for all uses.
Also read: What Role Does Artificial Intelligence Play in DevOps Efficiency?
No prioritization method= Friction, wasted time, and unnecessary Risk
It is unfortunately one of the main reasons that can bring about the golden standard that exists for vulnerabilities and their prioritization. Every company and others are rightly looking for the same organization. It rates the recent DevSecOps insights reporting the best challenge implementing the running their AppSec programs. The vulnerabilities of the prioritizing are about becoming the issue that often takes a lot of standards. Along with that the agreed practice of the conundrum makes the development teams one of the best attempting features.
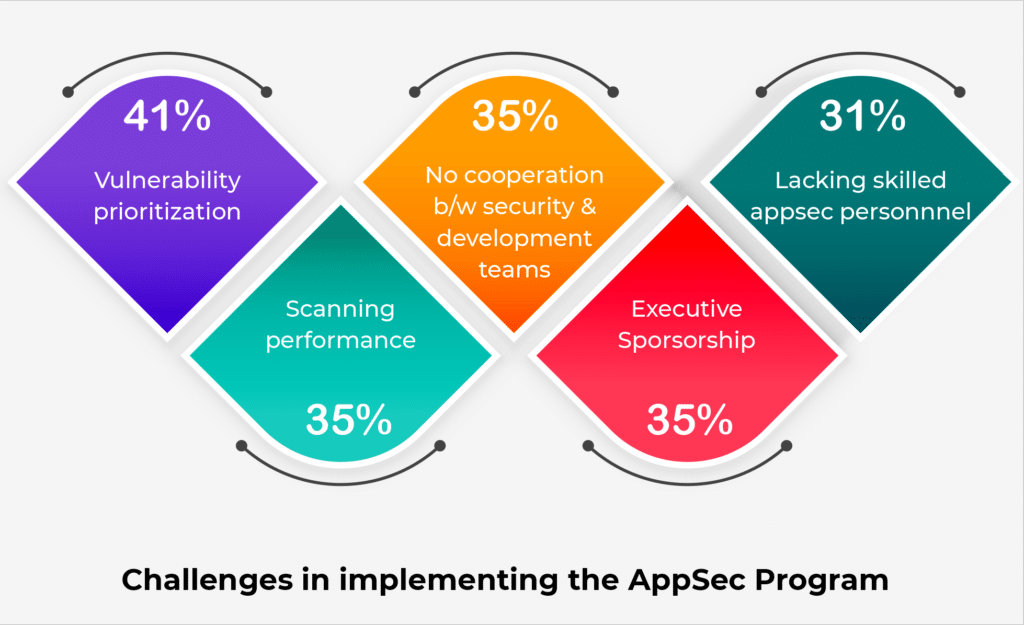
In the meantime team, all are deciding on the ad-hoc decision. It is all about the separate features which are about deciding to maintain the guidelines. The guidelines deal with the risk of letting the most critical vulnerabilities through the cracks which are all about the critical acceptances. It helps in maintaining the time wasting no time by avoiding more friction and problems with a single outlet with the prioritizes and the scheduling of the time. The undesirable schedule can be well-maintained and handled in a variety of various ways.
Prioritization: going one step further than detection
Vulnerability prioritization needs to be fixed first endless list of security slowing down the speed of development. The organization finds a way to keep prioritizing the seamless and endless list and security alerts currently required with the address and slowing the pace of the development. There is no need to create unnecessary risks by prioritizing the features. Each company and sometimes even different teams work within the same guidelines that can prioritize in different ways. It develops and reveals the application security and the professionals that rate the vulnerability along with the prioritization of the organization.
Prioritization vulnerabilities have become one of the issues that often take up a lot of development security outfits’ time. This happens to the lack of the standard and agreed-upon best practice comes to determine whether vulnerabilities are fixed first. The solution to the issue of vulnerability deals with solid prioritization along with technology building and saving time and resources which includes the debates and vulnerabilities that are fixed first and foremost.
While the next generations of the vulnerabilities are considered, it impacts the system that is addressed with possibilities. The detection tools used in the vulnerability enable the teams to move out one step further along with the addresses which prioritize the system and its working too high. Time management is another important factor that is used effectively to plan the days of success and work with less effort and then make the most out of the limited time.
Getting Vulnerability Prioritization Right
While looking into the future of automatic prioritization and actionable insights, you can understand how remediation advice is so important. There are benefits of prioritizing the application and securing the detection which is created with future automation. The detection tool easily prioritizes the remediation and also the security impacting the code by providing the exact location which developers can easily get the scope and locate it through the addresses used.
Once the location is maintained and detected the processing starts its activity. The biggest security and the threat to the applications happen to be one of the best. There is no more to waste any time with friction releasing the secured products and also on time. The prioritization process includes organizational and interesting concepts to work on. The priorities and the vulnerabilities matter a lot when it is about taking a better scope to work ahead with the outcome.
Also read: Static Application Security Testing: SAST Basics
Prioritizing the cyber threats enhancing digital security
It is time to take your security to the next level as the organizations are prioritizing information sharing and the steps to optimizing what you already need. Managing the security and the vulnerabilities to different levels is no more an easy task. Thus it is better to discuss how to pen test and then decide on the right objective. Every concept is enhanced, prioritized, and then validate by the efforts of remediation. Users can prioritize the cyber threats to enhance the digital security of the business or the priorities.
Prioritizing cyber security to the next level with cyber security is the real objective. It is a real concern as well. Most businesses are turning into competitive, digitalized, and stuffed with cyber security. As per the cyber security report, prioritization has been enhanced and given more scopes to the advent of mobile technology, internet, and wearable securing the business brands behind searching for finding the loopholes that can be exploited in the system.
The cybercriminals are not too simple and they implement the denial of the service attack along with the leaves. Companies are trying to figure out the stakeholders and find the right kind of stake holding task. Users must take care of the threats and events with the various securities. It is to deal with the threats quickly and also efficiently group in terms of major functions in relation and composition at IT.
Read about: How to Outsource App Development in 2025 – Crucial Factors
Teams and expert attracts attention
Teams and expert professionals consider attracting the attention of the target for the hackers. The open source vulnerabilities act as additional parameters and also work upon increasing the popularity despite determining the factor along with the vulnerability of the risk level. It is upon which the common practice of the organizations can handle the hefty backlog of the alerts that is liable to wipe off the slate creating different kinds of vulnerabilities.
It is essential to understand which priority is important? The science speaks like the developers must figure out the way to become a zero on the security vulns presenting the most risk with quickly addressing the speed of the development. There happens an exponential rise in the volume were grabbing security along with vulnerabilities. There happens a heightened focus on the detection along with the remediation of the security vulnerabilities as early as possible.
Prioritization of the vulnerabilities
The prioritization of the vulnerabilities spends a lot of vulnerabilities. The understanding of the prioritization methods includes currently the common surveyed 300 of the users and the customers that can avail the popularity of the vulnerable open the sourcing of the component and also vulnerabilities, disclosure date and the ease off the remediation respectively.
Experts take over 100 most common open sources of vulnerabilities which have about artificial intelligence gathered with the hacker communities. We can gain insights into the effectiveness of the common prioritization methods measuring the hacker and its community weaknesses.
Vulnerability and its severity
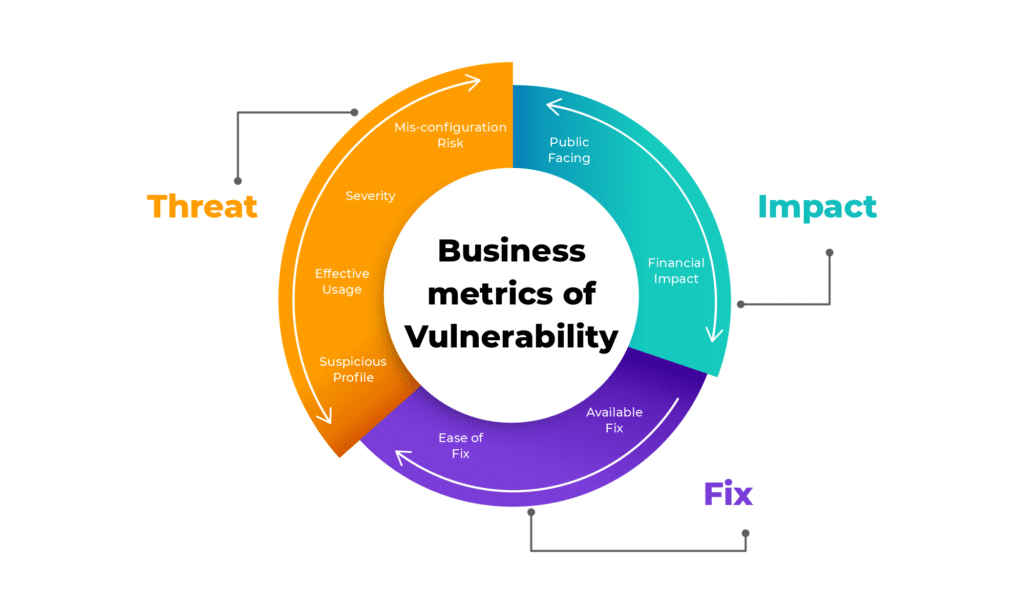
Vulnerability and its severity are also another important factors that discuss common vulnerability scoring system and the score at first prioritized since it the easily accessible with seemingly straightforward maintaining the parameter. It shortens the long list of security and its vulnerabilities that need to be addressed at a high rate as well as critical.
The organization needs to add the additional parameters to say that it ensures the addresses and figures the right issues while wasting time on security vulnerabilities posing less of the threat as they have got a high severity score. The system architecture and the application type appear to be one of the best matches which are about clearing the most essential features.
The vulnerabilities include the threat to the critical application relating to business data, confidential data with intellectual property, and financial transactions. It is one of the extremely significant considerations with challenging and solvent issues that help to create the methodology of one-size-fits-all along with subjective variables and the user audience as per the audience and mobile app or the web application.
Final Verdict
The more the popularity of the open source component, the more turns out to the exploitation of the opportunities provides to the hackers. In the beginning, there was hardly any correlation between the level of discussion and the popularity of the hacker communities. The common open source security vulnerabilities came up with hacker communities. What are you waiting for? Get help from Amplework right away.



 sales@amplework.com
sales@amplework.com
 (+91) 9636-962-228
(+91) 9636-962-228