Cyber Threats in 2024: Latest Statistics and Best Practices for Businesses
The expansion of innovative techniques makes businesses completely rely on digital practice. For the smooth running of these virtually advanced technologies, cyber security plays a significant role. Cyber threats have been a major concern in recent years due its enhanced attacking capabilities. The practices followed by these cyber threat actors are becoming more sophisticated and complex. The motives behind these attacks can range in a variety. These can be financial gain, political espionage, and others. The occurrence of these applications can lead to many consequences for the business procedures. Which can be loss of confidential information, property loss, negative market image, and consumer dissatisfaction or loss. To deal with these cyber security impacts one needs to invest in different costly assets. These solutions can directly impact the growth factors of the businesses.
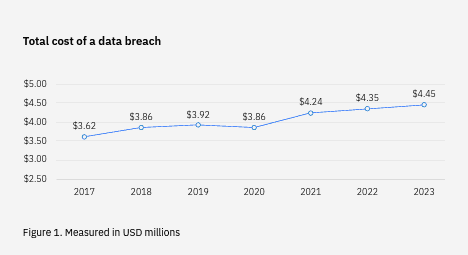
In this context, the research data by IBM Cost of a Data Breach Report 2024 highlights the cost criteria of these cyber threats. As shown in the below figure the total cost of a data breach has been increased to $4.45 million on a global scale. It is estimated that the cost of these attacks has increased in a rapid way. Which represents a harmful condition for businesses. This increasing cost shows the level of complexity is increasing with the increase of technical innovations.
Blog Highlights
The main purpose of this blog is to provide effective knowledge of cybersecurity issues. The major highlights of this blog are the major cyber security threats for business in 2024. The best practices from which these threats can be resolved. Cyber threats have the aim of destroying business procedures in many ways. This blog is all about the things that are essential for a business to stay away from security threats.
Trendy Cyber Security Threats for Business in 2024

Cyber security is globally recognized as the process of providing protection to digital devices. Whether it belongs to an organization or an individual. The emergence of cyber attacks can lead to different consequences. This section of the blog presents major threats to application security and development.
1. Ransomware
These attacks remain a significant cybersecurity threat. Ransomware is malicious software that encrypts files. That demands payment for decryption, potentially causing data loss and financial harm to businesses. To protect against this threat, businesses must take proactive measures. Which includes robust backup and recovery solutions, well-defined incident response plans, employee training to recognize ransomware risks, keeping software updated, strengthening network security, and implementing multi-factor authentication. Also, regular security audits are also vital for identifying and addressing vulnerabilities. These steps are essential to safeguarding business data. In the ever-evolving cybersecurity application development and practices.
2. Phishing and Social Engineering
These are considered the major cyber-attacks that use the trick of manipulating individuals. With the help of faking the main source of services. In this fake websites are created to extract personal information and use this information in a negative manner. The emerging rate of these cyber attacks is continuously increasing in 2024 and contributing to the digital environment more risky.
3. Remote Workflow Security Issues
To secure the software development lifecycle for remote and hybrid work environments, organizations should adopt robust security measures. That includes VPNs, multi-factor authentication, and endpoint/mobile device security. Employee education on risk identification, cybersecurity best practices, and maintaining secure password habits is equally vital.
4. Security In the Internet of Things (IoT)
IoT security plays a pivotal role in safeguarding cloud-connected devices from the potential threats of data breaches and malicious attacks. Establishing proactive security measures, such as the imperative practice of changing default passwords. Serves as a primary defense against threats like the notorious Mirai malware. In this ever-expanding realm of interconnected devices. It is incumbent upon original equipment manufacturers (OEM) and application security for developers as a top priority. By doing so, they can effectively fortify the security of these inherently vulnerable devices. Against the ever-evolving landscape of cyber threats. In addition to password management, considerations like regular software updates, robust encryption, and network monitoring. Also contribute to a comprehensive IoT security strategy.
5. Cloud Security
Cloud security is a collaborative effort, with shared responsibilities between the service provider and the customer. The provider shoulders the responsibility of securing the underlying infrastructure, managing access control, and ensuring the patching and configuration of hosts and networks. In contrast, the customer has a critical role in managing users and their access privileges, safeguarding their cloud accounts, implementing data encryption and protection measures, and ensuring compliance with industry and regulatory standards. This division of responsibilities ensures a robust and comprehensive approach to cloud security, where both parties play a pivotal role in safeguarding data and infrastructure.
6. Cyber Espionage
Cyber espionage is the unlawful retrieval of sensitive data or intellectual property with intentions of economic, competitive, or political advantage through cyberattacks. As we move into 2024, this threat continues to loom large. Prominent instances, like the Operation Aurora attack targeting Google’s Gmail, serve as stark reminders of the persistent need for organizations to bolster their defenses. To counter the menace of cyber espionage, proactive measures such as network segmentation and intrusion detection systems should be prioritized. Moreover, collaboration with law enforcement agencies is imperative to mitigate the risks and consequences associated with cyber espionage.
7. Supply Chain Security
Supply chain risk management encompasses the assessment and mitigation of potential risks across the entire supply chain, encompassing external suppliers, logistics, and technology partners. This multifaceted approach involves the identification of vulnerabilities and the subsequent implementation of risk mitigation strategies. It entails a combination of risk management practices, fortified cyber defense mechanisms, and strict adherence to pertinent government regulations and industry protocols. As global supply chains become more intricate, effective risk management becomes indispensable in ensuring operational resilience and safeguarding against an array of potential disruptions.
8. Identity and Access Management (IAM)
IAM security is an integral component of modern IT security infrastructure. It revolves around the administration of digital identities and the regulation of access to critical data, systems, and resources. IAM blends the implementation of comprehensive policies, advanced technologies, and strategic programs with the overarching goal of mitigating identity-related risks and enhancing overall business security. These IAM solutions serve as a linchpin in an organization’s ability to curtail risks, maintain regulatory compliance, and streamline operational processes. By effectively managing digital identities and access control, businesses fortify their cybersecurity posture and ensure the confidentiality, integrity, and availability of vital data and resources in an increasingly interconnected digital landscape.
9. Blockchain Security
Securing a blockchain ecosystem necessitates a multifaceted approach, which encompasses comprehensive risk assessments, the adoption of robust cybersecurity frameworks, stringent security testing, and the practice of secure coding methodologies. These combined efforts are pivotal in shielding the blockchain infrastructure against online fraud and various cyber threats, ultimately contributing to the sustained application security and development and maturation of blockchain technology. Blockchain security remains paramount in maintaining the trust and safeguarding the integrity of digital transactions in a dynamic and ever-evolving digital landscape.
10. 5G Security Issues
The realm of 5G security plays a pivotal role in safeguarding high-speed mobile services that cater to billions of devices, including the Internet of Things (IoT). Ensuring secure 5G experiences involves the implementation of advanced authentication mechanisms and the enhancement of subscriber protection measures. However, to unlock the full potential of 5G technology, it’s imperative to address security risks stemming from unsecured IoT devices and sensors. These risks must be meticulously managed to create an environment where the benefits of 5G can be fully harnessed, fostering innovation and connectivity while ensuring data and network integrity in this era of rapid technological advancement.
11. Cybercrime As a Service
This remains a menacing business model in 2024, enabling malicious actors to provide hacking services and tools easily accessible on the dark web. What’s particularly concerning is that it empowers even nontechnical individuals to initiate cyberattacks. To counter this looming threat, organizations must place a premium on their defense mechanisms. This involves a multi-faceted approach, including comprehensive employee training to enhance cyber awareness, leveraging threat intelligence to stay ahead of evolving threats, and bolstering incident response solutions to mitigate the impact of cyberattacks. CaaS necessitates a proactive stance in cybersecurity, as businesses navigate this ever-evolving digital landscape and work to protect their sensitive data and critical systems.
You May Also Read: All You Need to Know About Cyber Security Compliance
Best Practices for Businesses for Preventing Cyber Threats
Cyber threats are not treated as recently emerging digital vulnerabilities and have been present in the market from the start of digital innovations. With the advancement of technologies, the complexities of cyber threats are also increasing. In the current times, business needs to adopt effective mitigating practices to deal with these issues. Some of these best practices are as follows.
Formation of Accurate Cyber Security Strategy
Conducting a cybersecurity audit for your business is a crucial step to evaluate your current security landscape, examining existing measures, employee awareness of potential risks, and the layers of protection for networks and data. Subsequently, crafting a strong and people-centric cybersecurity strategy is vital, with a particular emphasis on safeguarding sensitive and proprietary information. This approach ensures that the strategy prioritizes the well-being of employees and end-users, aligning security practices for their benefit and overall protection.
Updating and Integrating Security Policies
For the regular maintenance of robust cybersecurity. Businesses can look forward to regularly updating their policies and can accommodate evolving technology and data handling methods. These policies are a foundation of security, necessitating periodic revisions and employee training. The adoption of a zero-trust architecture, involving continuous validation and tools like multi-factor authentication and password re-entry prompts, proves effective in enforcing these policies, ensuring resilient defenses against emerging threats.
Establishing Regular Contact with Cybersecurity Audits
Regular cybersecurity audits are a prudent practice to ensure organizations are effectively safeguarding against evolving and sophisticated risks. These audits, recommended at least annually, are particularly crucial for businesses managing personal data and large datasets, often conducted biannually. Apart from compliance and legal adherence, cybersecurity audits serve to streamline tools and processes, strengthening an organization’s resilience against cyber threats.
Collaborative Approach with the IT Department
Business leaders can proactively manage and prevent cyber threats by collaborating closely with their IT department and support staff. These preventative measures vary based on factors like organization size and industry. Engaging a cybersecurity consultant in tandem with the IT team helps identify tailored strategies, including cloud technology adoption, security measures, and comprehensive plans for employees and end users.
Monitoring of Third-Party Users
Third-party users who can access your organization’s systems and applications possess the potential to compromise your data, whether through intentional actions or otherwise, potentially leading to cybersecurity breaches. By closely monitoring user activities, implementing access restrictions to protect sensitive information, and utilizing one-time passwords, you can effectively identify malicious actions and proactively prevent breaches.
Sourcing IT training and Education within the Organization
Businesses should implement these cybersecurity best practices, with a key role assigned to employees in maintaining robust password security and policy adherence. To ensure these practices are followed, it’s essential to provide cybersecurity and IT training during employee onboarding. Continuous education, IT support, and routine security updates should seamlessly integrate into their daily workflow. Raising employee awareness, clarifying their compliance with cybersecurity protocols, and elucidating the significance of these practices with explicit guidelines are vital steps for effective cybersecurity management.
Wrapping Up
In 2024, cybersecurity is all about understanding the latest statistics and implementing best practices to protect businesses from evolving cyber threats. The landscape has become increasingly complex, with motives ranging from financial gain to data theft, making it imperative for businesses to act. Our blog serves as a beacon of knowledge and guidance for users. Offer accessible insights and proactive steps to safeguard your business from cyber threats. With information as your first line of defense, staying informed and adopting best practices can help establish robust digital fortresses
At Amplework, a trusted leader in mobile app development with over 5+ years of immersive experience, we understand the critical importance of cybersecurity. Our dedicated team consistently exceeds client expectations, earning a reputation for reliability and trustworthiness. We’ve achieved significant milestones by supporting various organizations while adhering to the highest standards of cybersecurity. Explore our website to discover the exceptional cybersecurity services we offer. Partner with Amplework to embark on a transformative journey toward protecting your business from cyber threats.
Read More:- Cyber Security Essentials



 sales@amplework.com
sales@amplework.com
 (+91) 9636-962-228
(+91) 9636-962-228