Enhancing Security of Data using AES Cryptography
Symmetric Key Cryptography:
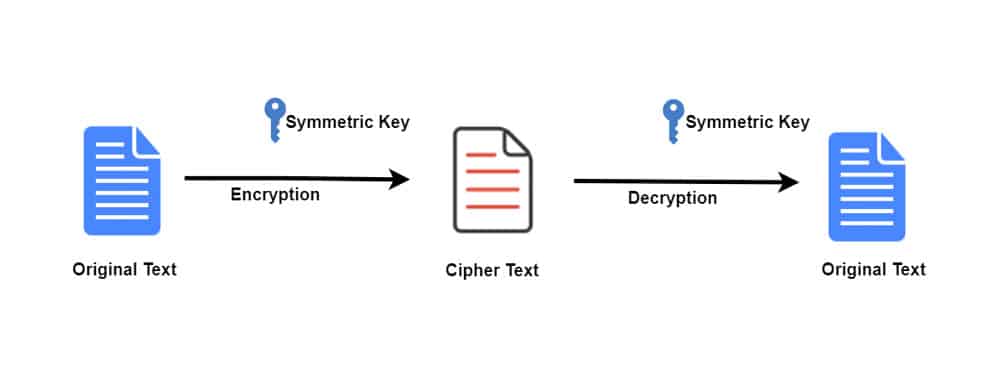
In Symmetric-key encryption single key can encrypt and decrypt data. The distribution of keys should be done before transmission to happen between two parties. This Key plays an important role in encryption and decryption. The use of a weak key in the algorithm can easily lead data for decryption. The size of the key determines the strength of such type of key encryption. Symmetric algorithms are of two types: block ciphers and stream ciphers.
The first type of symmetric algorithms i.e., block ciphers are operating on data in groups or blocks. Examples are Data Encryption Standard (DES), Advanced Encryption Standard (AES), and Blowfish. The second types of symmetric algorithms are Stream ciphers are operating on a single bit at a time. RC4 is a stream cipher algorithm. Encryption algorithms consume such amount of computing resources such as battery power, CPU time, etc. Asymmetric key (or public key) encryption can solve the problem of key distribution.
Read more: How to develop a health care app like “Practo”?
Asymmetric Key Cryptography:
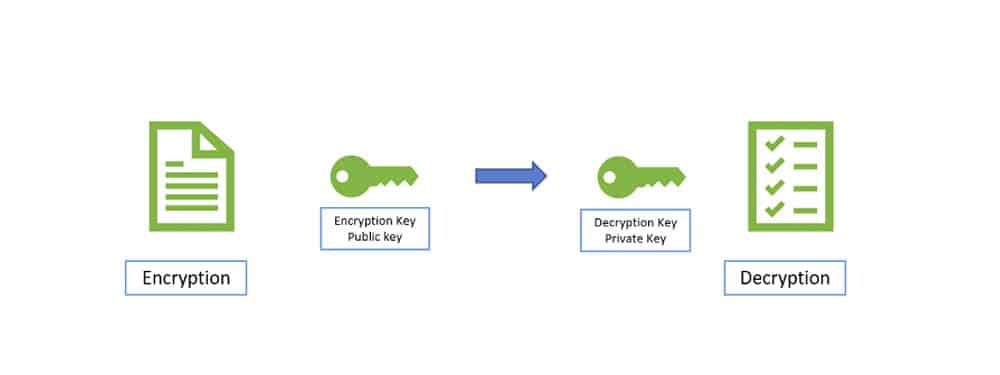
In Asymmetric key encryption, double keys are usable; private keys and public keys. The public key is for encryption while the private key is for decryption (e.g. Digital Signatures). The public key is for the public and private key to the user. There is no distribution before transmission. Asymmetric encryption techniques comparatively 1000 times slower than Symmetric techniques since they require more computational processing power.
.AES
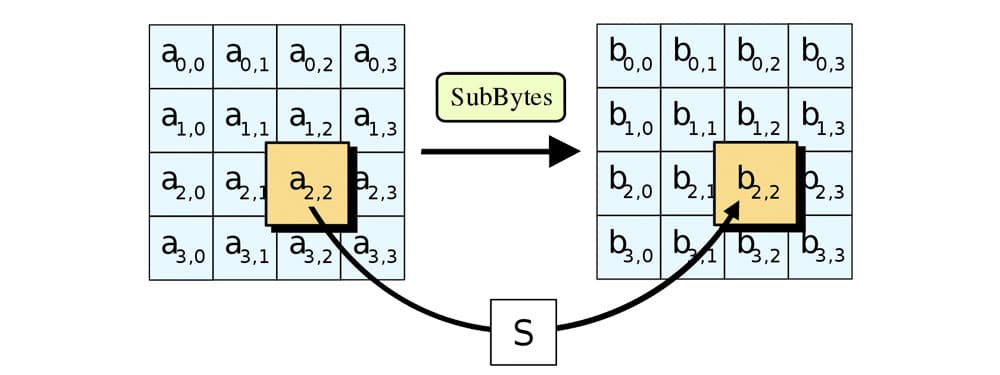
Advanced Encryption Standard (AES) also termed as the Rijndael algorithm is a symmetric block cipher. The security of DES has been hindered due to advancements in computer processing power. NIST serves the purpose to define a substitution for DES that can be applied in non-military information security applications by US government agencies. [6] AES is a block cipher with 128 bits of a block length.
AES allows for three different key lengths: 128, 192, or 256 bits. Processing for encryption consists of 10 rounds for 128- bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256- bit keys. Processing for each round includes one single-byte based substitution step, a row-wise permutation step, a column-wise mixing step, and in addition the round key. The order in which these four steps will execute is different for encryption and decryption. AES encryption is fast and flexible. You can implement it on different platforms especially in small devices. AES has best for many security applications


 sales@amplework.com
sales@amplework.com
 (+91) 9636-962-228
(+91) 9636-962-228