The Role of Full-Stack Development in Enhancing Cybersecurity Measures
In the tech-based landscape of the modern world, where mobile applications are handling business operations more accurately and efficiently, the need for full-stack development in cybersecurity has never been more crucial. In this digital realm, the role of cybersecurity is extremely important as these cyber threats or vulnerabilities can cause serious damage or harm to your business’s data, compromising your brand’s reputation and user’s trust in your business. Also, they can be a major reason behind the legal actions against your brand. That’s why business organizations can no longer afford to prioritize features and functionalities over security. They majorly focus on building robust defense and security mechanisms for their business solutions. This is where the expertise of full-stack app development in cybersecurity is highlighted, putting an undeniable impact on crafting more reliable, efficient, and secure solutions for businesses.
Unlike deploying separate teams for crafting a mobile or web solution, Hire full-stack developers completely understand the entire spectrum of mobile application development. That initially gains momentum through crafting a user interface and ends through working on the server-side operations. This holistic development approach of full-stack developers implements security mechanisms into the specifically crafted mobile applications and web solutions according to the varying needs and requirements of the businesses. Since mobile applications and web solutions span both the backend and frontend, security implementation is a priority. However, implementing the security measures can also be a challenging task as each layer possesses a unique and well-defined challenge and comprises vulnerabilities that the developers must address or deal with to ensure the complete protection of mobile apps against cyber threats.
Blog’s Aim
In this blog, we will be discovering how full-stack development in cybersecurity can be leveraged to strengthen cybersecurity measures, discussing aspects such as secure coding practices, data encryption, and threat detection. Also, we will be discussing the fact that how full-stack development services are crucial, especially when it comes to implementing a robust protection mechanism against potential cyber threats and vulnerabilities associated with your business solutions when it is crafted separately by the frontend and backend developers.
Addressing Some Statistical Research Considerations
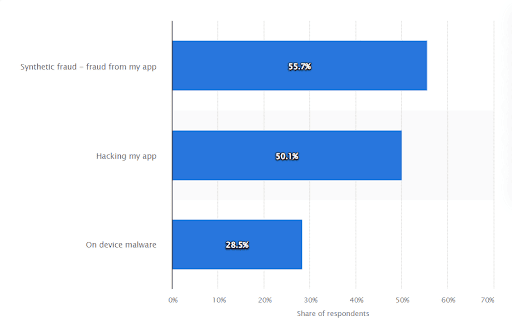
We all are aware that numerical or statistical data has its significance and relevancy. This data is considered factual evidence to prove the fact about an increasing number of emerging cybersecurity threats for mobile applications. According to data from the survey, available on the most reliable platform that is “Statista” clearly stated that cyber fraud was the most concerning security issue for mobile application development. According to this study, more than 55.7% of respondents have reported synthetic cyber fraud that comprises merged pieces of client’s personal information such as names, emails, and social security numbers from a wide range of sources. The next issue that was reported was that of hacking of their mobile applications by third-party users by almost 50% of the users. Finally, 28% of respondents appear to be worried about their on-device malware which was a threat for them.
Benefits of Full-Stack Development in Cybersecurity App Development
As the field of cybersecurity is safeguarding a wide range of mobile and web solutions against several forms of cyber threats. Here’s how the full-stack development services are beneficial for ensuring the implementation of robust security standards according to your business solutions and their requirements:
1. Versatility:
The Full-Stack Development solutions approach involves building both the ends that are backend and frontend. So the developers involved in the same are proficient in working with different tech stacks and programming languages. This versatility allows them on a variety of aspects of a mobile or web solution, one amongst them being cybersecurity, allowing them to implement completely enhanced and multi-layered security solutions for safeguarding business applications against cyber threats.
2. Crafting Secure Web Solutions:
One of the additional key benefits of full-stack app development in cybersecurity is their ability to craft robust, efficient, and secure web applications. Ensuring the complete integration of the robust security features into the application starting from the initial design phase to deployment. They facilitate the implementation of secure coding practices, thorough testing, and addressing the available vulnerabilities to assure complete security.
3. Efficient Functioning:
When compared to a team of both frontend and backend developers the full-stack developers can work more rapidly and efficiently as they don’t need to wait or rely on other teams to move between both the frontend and backend. Instead of juggling amongst both these the full-stack developers can easily and rapidly craft your desired mobile and web solutions according to your needs and requirements.
4. Proactive Threat Detection & Mitigation:
The holistic approach of full-stack developers in cybersecurity, leveraging their knowledge base to implement security measures for business solutions, enables them to address vulnerabilities effectively and write secure code. They identify potential threats using testing mechanisms such as penetration testing and code scanning, leading to reduced vulnerabilities and mitigated risks of data breaches.
5. Facilitating Secure Development Practices:
Hire full-stack developers can effectively utilize highly secure frameworks and libraries, saving development time and ensuring adherence to implementing the security best practices. They can also automate security testing mechanisms within the development workflow, catching vulnerabilities early and finding a cure for similar data breaches often.
6. Rapid Threat Response and Recovery:
As we have already studied full-stack developers can easily and effectively diagnose the actual cybersecurity incidents, facilitating faster recovery against such cybersecurity threats by getting an idea about the affected components and also their actual dependencies as well. Offering the users a rapid threat response and recovery as well for the same.
7. Enhanced App Performance:
Securely crafted mobile applications by full-stack developers can be a game changer when it comes to the app’s performance and reliability. As these mobile applications consist of only a limited amount of vulnerabilities and issues, witnessing improved performance and stability for the same. This results in a better user experience and also reduces downtime as well.
The Diverse Ways How Full-Stack Developers Contribute to Cybersecurity
Contributing to the implementation of cybersecurity toward mobile and web development solutions can be a time-consuming task and also a challenge, especially when the dependency to craft a mobile or web solution relies on different teams for both the user interface and the backend. Here’s how the full-stack web development service providers contribute to cybersecurity implementation:
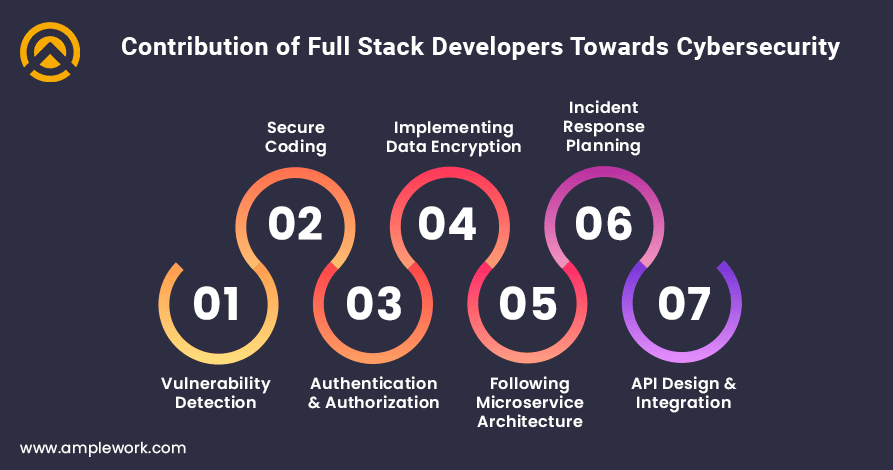
1. Identifying the Vulnerabilities:
The coding expertise of full-stack developers allows the users to scan the complete code to identify security vulnerabilities. By utilizing the techniques and penetration testing tools to remain updated on the latest emerging cyber threats to implement the security vulnerabilities quickly and rapidly without facing any hassles or issues as well.
2. Implementing the Secure Coding Practices:
When you hire full-stack developers in India, their expertise and complete knowledge about the implementation of security mechanisms act as anticipation for avoiding pitfalls or cyber threats like SQL injections, cross-site scriptings, and implementing insecure authentication mechanisms. As these are the major threats to mobile or web solutions and can cause serious damage to client’s data.
3. Implementing Authentication & Authorization:
Building and crafting a secure multi-factor authentication mechanism that adds a layer of defense against the unauthorized access of intruders or 3rd party users that are not authorized to access the same. Also implementing the authentication and authorization mechanisms can effectively safeguard the sensitive data exchange between the applications and components.
4. Implementing Data Encryption Mechanisms:
Implementing the encryption algorithms for both the stored and transmitted data available on the backend of your mobile or web solutions. Ensures the maintained privacy confidentiality and integrity as well when it is intercepted. Implementing such mechanisms also leads you to effectively maintain or manage your private and confidential data, protecting it from unauthorized access and data breaches.
5. Following Microservice Architecture:
Since the full-stack development process involved the creation of a complete application including frontend, backend, and database. Following the microservice architecture to break down the application into smaller, isolated services can effectively minimize the attack surface and also reduce the amount of potential damage in case of data breaches.
6. Incident Response Planning:
Hire full-stack developer can contribute to developing an efficient and accurate incident response plan to mitigate cyber threats swiftly and efficiently. They have the knowledge and vast skillset to monitor the complete mobile or web application, which allows them to effectively monitor the system logs to analyze the overall functioning and behavior, which helps them to identify suspicious activities at the early stages so that they can easily derive the mechanisms to efficiently mitigate them.
7. Secure API Design & Integration:
Full-stack development services providers facilitate the implementation of secured authentication protocols such as OAuth and OpenID Connect to build the application program interface with granular access control mechanisms and implement the rate-limiting mechanism. Also for the same, they can effectively utilize secure data formats like JSON web tokens to facilitate secure information exchange.
Concluding It
While concluding this blog, we have understood the value proposition of full-stack developers in the implementation of cybersecurity during mobile application development. Implementing the security measures for cybersecurity through their holistic understanding, agility, and ability to seamlessly integrate security across the different mobile app development stages. As the full-stack development company incorporates a dedicated approach that initially begins with the requirement analysis to address the vulnerabilities across the entire application. Crafting solutions that are a combination of robustness, security, and reliability. Helping you build brand trust amongst your targeted audiences.
Amplework Software, your preferred Ai development agency in USA offers you a range of secured, robust, and reliable full-stack development. With our extensive knowledge of the latest tech stack, our team of experts delivers solutions specifically tailored according to your business’s industry-specific requirements through their collaborative approach. We also possess competency in implementing cybersecurity measures for businesses to maintain and manage privacy and confidentiality.
Also Read: All You Need to Know About Cyber Security Compliance
Frequently Asked Questions
Why Considering Cybersecurity is most important when you create a mobile or web solution?
Cybersecurity is one of the most crucial elements that effectively safeguard different forms of available data against theft, loss, and also unauthorized access. It can be personal information, payment details, pins, and passwords, business information system data, and also personally identifiable information. Considering the implementation of cybersecurity measures can be a game-changer as it also prevents your mobile or web solutions against various forms of cyber attacks as well.
Can a full-stack developer possess expertise in securing legacy applications?
Yes, however, there are some additional challenges like understanding the existing architecture, identifying the vulnerabilities, and integrating the desired security measures while minimizing the disruption caused by any sort of cybersecurity risks while minimizing disruptions that require careful planning and collaboration. Full-stack developers can effectively maintain and manage such issues effectively and efficiently.
Are there any specific security frameworks or libraries recommended for full-stack developers?
Yes, there are several options exist, depending on the technology stack used. It totally depends on your project’s requirements. However, the popular choices are Spring Security for Java-based applications, Laravel Sanctum for PHP, and Django REST framework for Python-based projects. You can choose according to the project’s complexity, size, and security requirements for the same.
How much time does it take to create a secure mobile application by full-stack developers?
The timing and cost completely depend on factors such as the requirements of features and functionalities, resources involved in the project, the complexity of the project, and also the feedback of the users. However, the full-stack app development approach can effectively and rapidly build your desired mobile or web solutions with ease and efficiency.


 sales@amplework.com
sales@amplework.com
 (+91) 9636-962-228
(+91) 9636-962-228