Static Application Security Testing: SAST Basics
SAST is to prioritize and also create onboard applications and also analyze the scan resulting in the right outcome. It provides the governance along with the training procedure. Static Application Security testing SAST Basics includes in it some statistically improved security vulnerabilities which can make the organizations apply with susceptibility. The SAST scans the application before the coding is compiled. This process is also entitled to white box testing.
What is SAST?
It is considered one of the most mature kinds of web applications that speed the application along with its movement. The process is also called white-box testing. The source code gets analysis from the inside while the key components are at rest and are not put to any use.
It is set to the technologies that are highly defined and analyzed with the right application source code. Static Application Security Testing has its pros and cons. All you need is to understand the work, strengths, and weaknesses. Along with it includes how it can be improved and straightened.
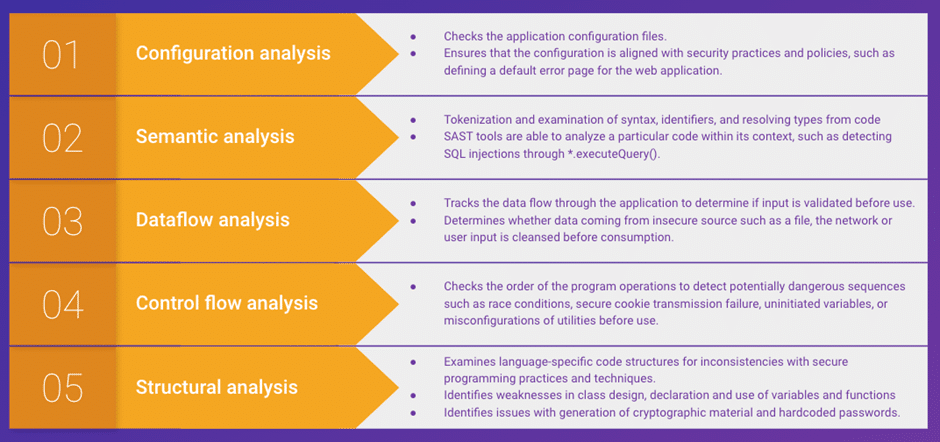
How does the SAST work?
Static Application Security Testing is all about how it scans the workings of the organizations and its coding and designing of the in-house activities. It also detects the flaws and also is one of the inductive weaknesses that can lead the security as per the vulnerabilities. The set of predetermined and reassigned rules are all assessed with the SAST to define the coding errors required in the source code that needs to be addressed and then reassessed to get a perfect outcome.
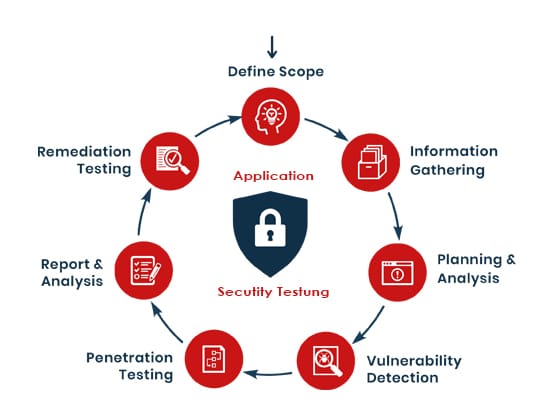
What SAST tools are highly suited for developers?
The SAST tools work effectively by the analysis that the application takes place along the inside and then test the areas which are to be put under control. These only work before the system takes its implementation and then require the application to deploy the same. Experts say that some lightweight tools can also be used to project the analysis. It is one of the best and the apt process to compile everything with a stable state.
Implementing the SAST tool usually requires the developers to create the best and perfect building model that gives the understanding of the tools and makes it understand by the interpretation only after the source code is determined. The CI or the continuous Integration servers are integrated more recently. It detects the flaws along with the IDEs. The organizational benefits are improved with the best strategies and also include something that can bring out the difference in them.
Read more: Importance of Mobile App Development For Fostering Business Growth
Why SAST is considered an important security activity?
The SAST solves great problems. The SDLC of the SAST means the software development life cycle which is used to work and apply the programs to get the task executed. The initial stages of the development quickly resolve the issues and identify the same to find the final release of the applications. The passing of vulnerabilities happens with much care. It is simply used to pass the code to the next level. It is to release the application with which it can fix and straighten the problems and move to the next level of the SDLC format.
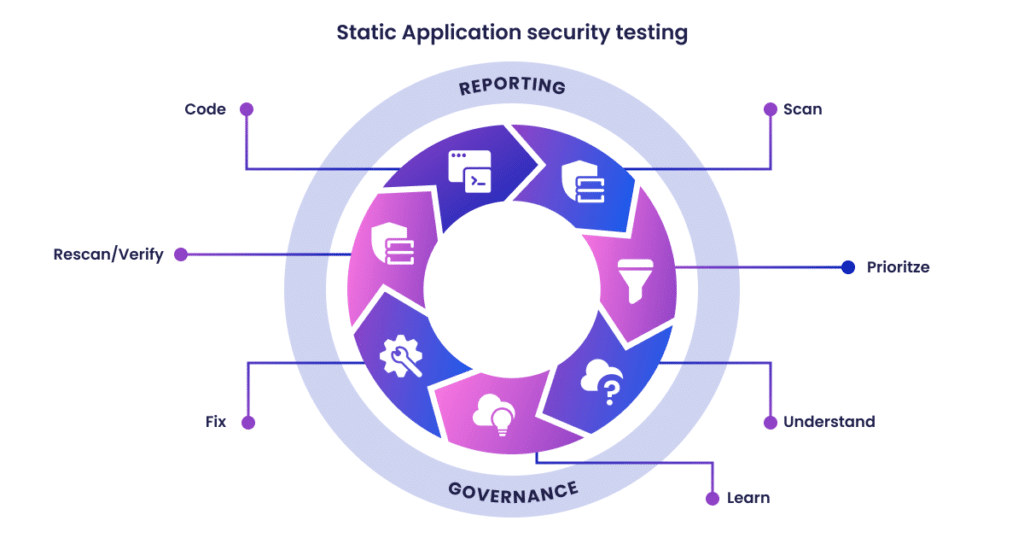
Steps to implement SAST
Choose the correct tool
Choose a static analysis tool capable of doing code reviews on programs developed in the programming languages you employ. The tool should also be able to understand the underlying framework that your product is built on.
Create the scanning environment and deploy the tool
This stage entails dealing with licensing requirements, configuring access control and authorization, and acquiring the resources needed to install the tool e.g., servers and databases.
Tool customization
Adjust the tool to meet the requirements of the company. By implementing new rules or changing current ones, you may, for example, customize it to decrease false positives or uncover more security flaws. Integrate the tool into the development environment, establish dashboards to follow scan findings, and produce custom reports.
Prioritize and onboard software
Onboard your apps once the tool is complete. If you have a big number of applications, prioritize which ones to scan first. All of your apps should eventually be onboarded and scanned regularly, with application scans synchronized with release cycles, daily or monthly builds, or code check-ins.
Analyze the scanned result
This stage entails triaging the scan findings to eliminate false positives. Once the list of concerns is complete, it should be recorded and distributed to the deployment teams for proper and timely resolution.
Provide essential training
Proper governance guarantees that your development teams are correctly utilizing the scanning tools. The SDLC should include the software security touchpoints. SAST should be included in your application development and deployment processes.
Read more: MVP Software Development: A Quickstart Guide to Success in 2023
SAST: know the PROS and CONS
There are ample benefits and disadvantages which are introduced so that users can easily get a clear concept about the improvising of the organizational benefit. The pro and cons of the SAST are as follows:
Pros of the SAST include the following-
Shifting Security Left
The integration of the security testing includes the earliest components of the software. The SAST or the Static Application Security Testing helps to shift the security testing left detecting the vulnerabilities in another proprietary code as well as the designs.
Ensuring the secure coding
SAST easily detects and reads the flaws complying with the coding standards and the best practice. The developing items include the order and the demand of the coding along with the security. There are simple coding errors that make sure that the security of the coding is ensured with the best results at any point in time.
Detection of common vulnerabilities
Various errors are detected with the vulnerabilities and the automated SAST tools can easily detect common security like smooth overflow and SQL injection, cross-site scripting, and other high confidence. Implementing the best tools help create the standardized model and the source code with a series of rule determining the best outcome.
Also read: Tracking Your Food Delivery Startup: A Comprehensive MVP Development Guide
Cons of the SAST include the following-
SAST or Static Application Security Testing is quite a matured technology that holds disadvantages and main weak points in the SAST. The following are the disadvantages and cons which include the following.
Doesn’t cover all the vulnerabilities
The access and the authentication are a little tough to detect the vulnerabilities. The SAS technology is fair enough to cover the run-time issuing the configuration issues that require the organization to implement the additional security. The testing tools are highly in demand that implements the additional security that all organization includes. The SAST tools don’t cover the open-source vulnerabilities.
The high number of false positives
High numbers of false positives have been spotted in the inclusion of the many such factors that have been in high demand in comparison to the configuration that controls the access and also the cryptography. SAST can never cover up the time of the issues as well as the configuration issues that require the organization to implement and add the security of the testing tools. The application opens up 60-80% of the concepts by opening the source of the components which leaves behind the substantial un-tested code that requires SCA tools.
Time-consuming
The concept of SAST can scan continuously and it takes around a few hours to complete the entire process. SAST verification with the potential vulnerabilities with a large codebase. It requires analysis to suspect with weakness counted among the security risk. Thus, SAST is a time-consuming concept.
Also read: Be wise & Prioritize: Taking Application Security to the Next Level
Sum-up
Because SAST technologies can detect security issues early in the development process, developers don’t have to worry about following best practices all the time, especially in time-critical scenarios. However, depending on how late in the software development life cycle SAST is incorporated, it may need a significant amount of effort to bring it up to speed. Traditional SAST tools will generate a large number of false positives, which developers must eliminate. And, if the system is built on a specialized programming language, there may not even be a SAST solution on the market to assist you with your security concerns. SAST solutions are, therefore, designed for developers effectively handle these challenges and provide a more fluid and efficient approach.
Contact Amplework Software for more information about SAST solutions.



 sales@amplework.com
sales@amplework.com
 (+91) 9636-962-228
(+91) 9636-962-228